Cybersecurity and SEO: Balancing Protection and Accessibility

The rise of remote work and rapid advancements in internet technology have made cybersecurity vital, especially for small- and medium-sized businesses (SMBs).
According to a recent study by BlackFrog, 61% of SMBs suffered at least one cyberattack in 2022. Even more alarming is that 87% of these respondents reported suffering multiple cyberattacks within a year.
The problem is that even though SMB owners and decision-makers are fully aware of the importance of cybersecurity measures, they don’t have the human or financial resources to make this happen.
That’s why, in this article, we’ll provide you with actionable cybersecurity tips and strategies to keep your business safe from cybercriminals without breaking the bank.
The SEO Implications of Website Security Breaches
What makes a cyber attack devastating for SMBs is that the consequences are as significant as they are far-reaching.
For starters, an average data breach resulting from a cyberattack costs a company $4.45 million.
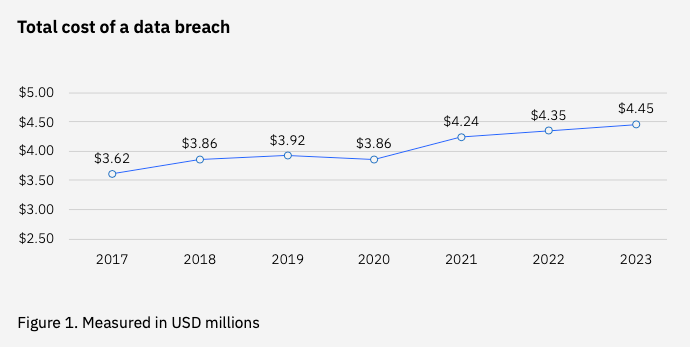
And that’s only the beginning!
Search engines will blocklist domains they consider suspicious, malicious, or dangerous to keep their users safe and prevent them from appearing in their search result pages (SERPs).
Browsers will also prevent people from visiting a website by displaying a message like this.
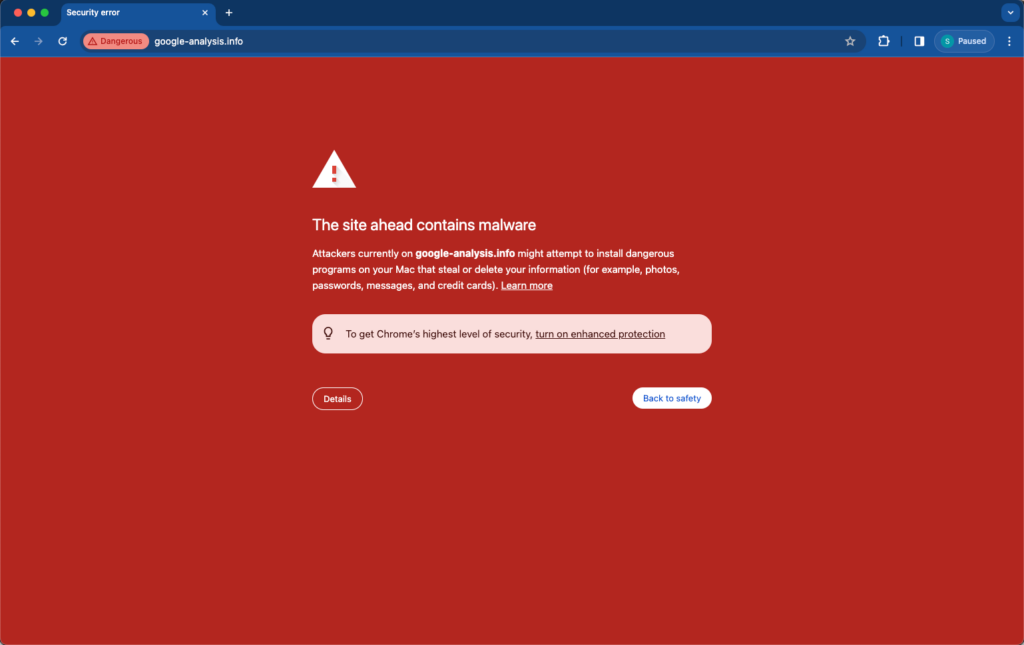
Not only will this cause a significant dip in SEO traffic, but it’ll also damage a brand’s reputation and credibility, so much so that new and existing customers will be discouraged from doing business with them.
The good news is that there are cybersecurity measures you can immediately implement to significantly minimize – if not eliminate – your chances of becoming a cyber attack victim.
Let’s take a look at these right now.
HTTPS: Enhancing Website Security and SEO Simultaneously
Website security is one of the SEO principles Google considers when evaluating your website’s page experience, which, in turn, impacts your search rankings.
One of the easiest ways to keep your website secure from cyber threats is by ensuring your website URL begins with HTTPS.
Unlike HTTP, HTTPS uses a specific protocol called an SSL/TLS certificate that encrypts all requests and responses happening on your website’s front and back end.
This ensures the information your website visitors and customers provide can’t easily be read and deciphered by cyber criminals, making it more difficult for them to hack your website and steal your customers’ data.
Optimizing SSL/TLS Certificates for Improved SERP Rankings
SSL/TLS certificates ensure that websites adhere to data confidentiality and privacy required in specific industries like finance and healthcare.
More importantly, SSL/TLS certificates assure your visitors and customers that your website—and their information—are secure.
In addition to checking your website’s URL, a website with an SSL/TLS certificate will show up with a padlock on Apple’s Safari.
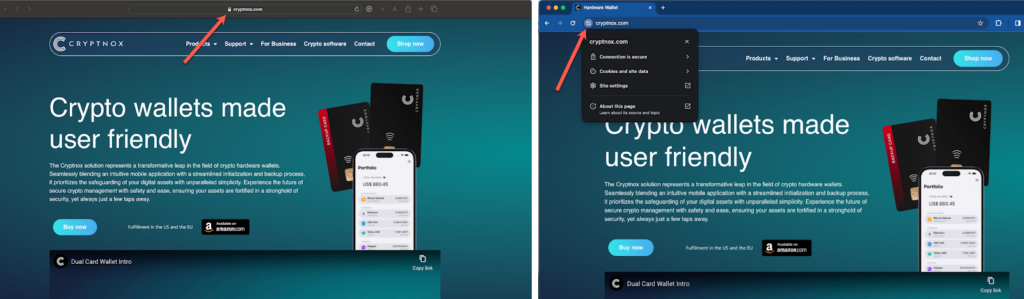
Cyptnox’s website’s SSL/TLS certificate on Safari browser (left) and Google Chrome (right)
There are three SSL/TLS certificate types:
Domain Validation (DV) Certificate
This is the lowest SSL/TLS certificate and provides only basic security for your website.
As such, it’s also the easiest to get because all you’ll need to do is confirm that you own your website’s domain through a phone call or via email.
Organization Validation (OV) Certificate
Compared to DV certificates, OV SSL/TLS certificates provide websites with a higher level of security, including the ability to encrypt sensitive information like credit card details and purchase history.
If you’re planning to apply for an OV certificate, be prepared to go through a screening process that involves providing proof of your business’s physical address and ownership.
Extended Validation (EV) Certificate
As you may have guessed, this SSL/TLS certificate has the highest security level. Financial institutions, hospitals, insurance companies, and healthcare providers commonly use it.
It’s also the most expensive and requires applicants to undergo an extremely stringent verification process.
On top of the security features available in the first two, EV certificates also protect your website and its users from unauthorized access from third parties.
This protects users when performing various online transactions requiring them to provide sensitive information like filing an insurance claim or requesting medical records.
Having the correct SSL/TLS certificate ensures that you’re providing your website visitors the level of protection and security they expect from businesses within your industry.
In turn, visitors will be more confident doing business with you, and search engines will reward you with higher SERP rankings and more SEO traffic.
Preventing Negative SEO Through Cybersecurity Measures
Negative SEO (aka “black hat SEO”) uses sneaky tactics to boost a website’s search rankings by damaging its competitors’ online reputation and rankings.
One of the most common tactics is link farming.
This negative SEO tactic creates backlinks from sites tagged as dangerous or malicious by Google and other search engines.
Tools like Ahrefs can help you identify and remove these potentially dangerous backlinks from your website.
Although you won’t find any specific tags specifying that backlinks from a particular domain are toxic, there are a couple of red flags to watch out for.
One is the referring domain’s site traffic.
If the website’s traffic is 0, it may be a sign that search engines and browsers are blocking users from visiting it.
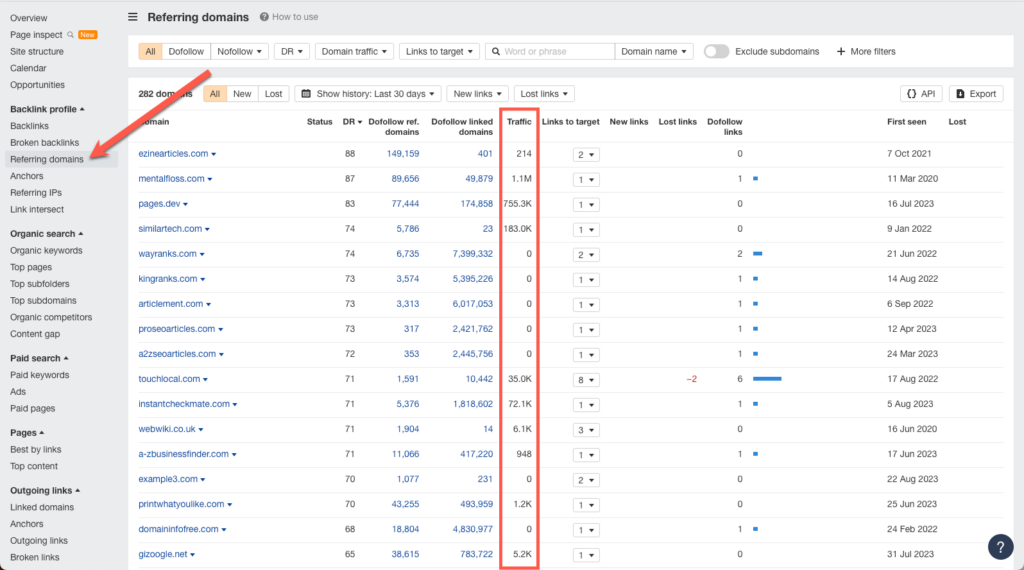
Another red flag to check is the URL anchor text pointing to your website.
A properly executed link-building strategy uses descriptive anchor texts with targeted keywords.
Link farming tactics don’t.
So, if you see random letters and “Empty Anchor” anchor texts listed, these could potentially be toxic backlinks.
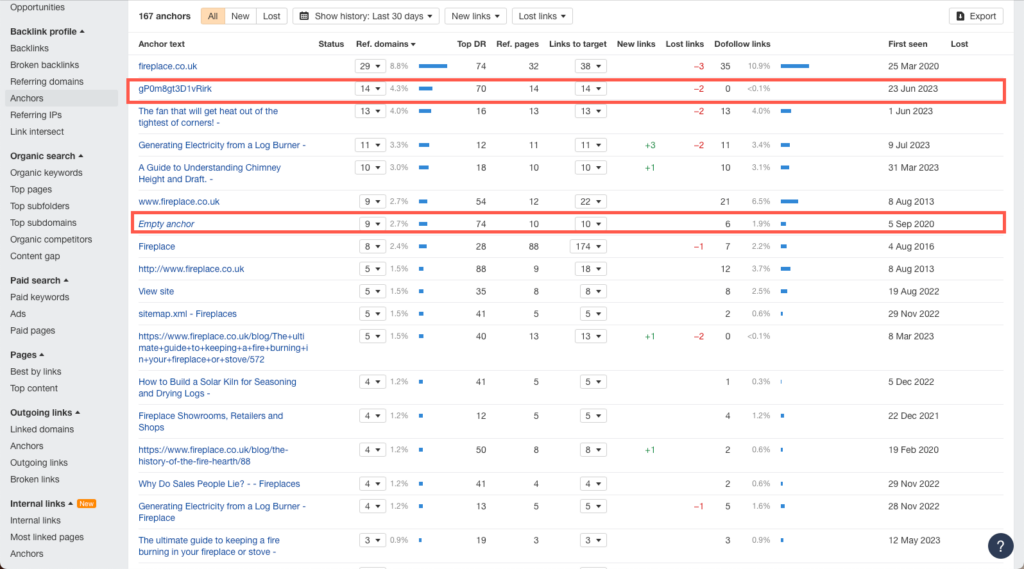
You can further check this by clicking on the dropdown menu next to the anchor text in the “Ref Domains” column.
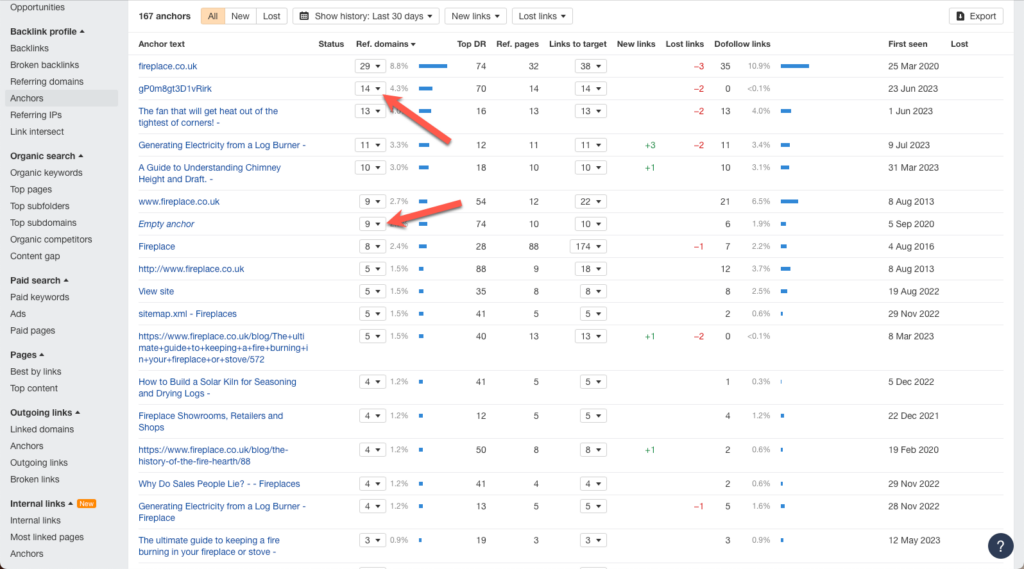
This will display a list of all the domains with backlinks to your site using that specific anchor text.
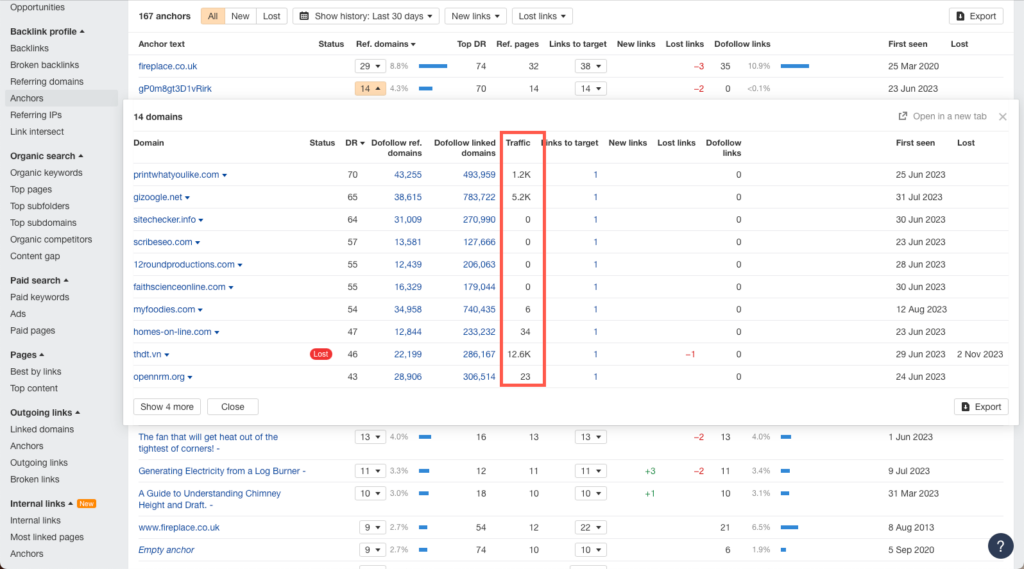
Again, check the Traffic column to see if any domains are not receiving traffic. If so, these may potentially be toxic backlinks.
You can then use Ahrefs’ Disavow Tool to submit these to Google so that search bots will ignore these backlinks so that they won’t be factored into your overall search rankings.
Secured Structured Data: Boosting Trust and SERPs
Schema markups help structure the different pages on your website in a way that search bots can easily access and understand its content.
Google uses this information to provide users with links to specific pages on your website under your homepage URL.
Take Novaalabs, for example.
Notice how its structured data allows Google to display multiple product pages underneath its homepage URL on its SERP.
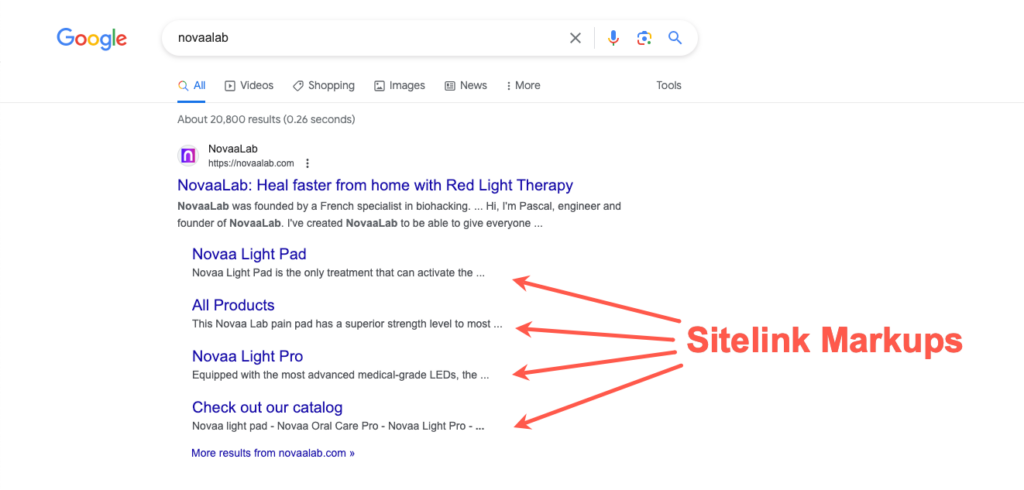
This makes the checkout process quicker and easier for Novaalabs’ new and existing customers.
And since Google would often list sites with sitelink schema markups at the top of their SERPs, Novaalabs increases its chances of its target customers visiting them instead of their customers.
If your business has a brick-and-mortar establishment, schema markups allow you to display detailed information about your business and appear on local search results.
The French Laundry, for example, uses schema markups that allow them to display both sitelink markups and local business profile information that includes customer reviews.
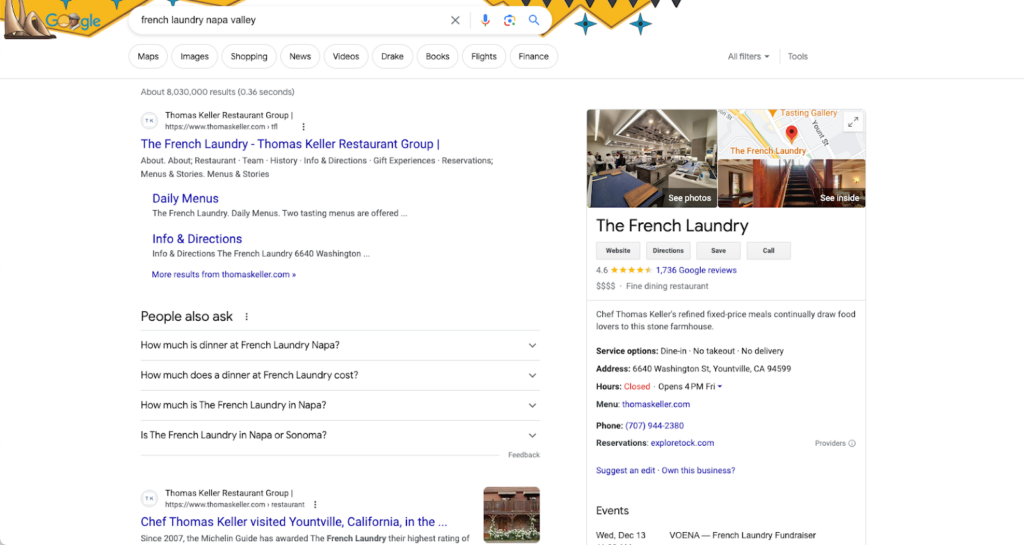
This allows them to transform the entire above-the-fold of Google’s SERP into one giant digital billboard promoting the restaurant, significantly reducing their target customers to dine elsewhere.
More importantly, displaying customer reviews and ratings helps the restaurant build a level of trust that will convince them to dine at this restaurant. It also increases the chances that diners will spend more once they get there.
However, schema markups are still code your SEO specialist creates for your website or generated by a plugin. This makes them prone to errors and vulnerabilities that cybercriminals are eager to exploit.
That’s why, before using it, make it a point to test it using Google’s Rich Results Test Tool to check your schema markup for errors, warnings, and vulnerabilities.
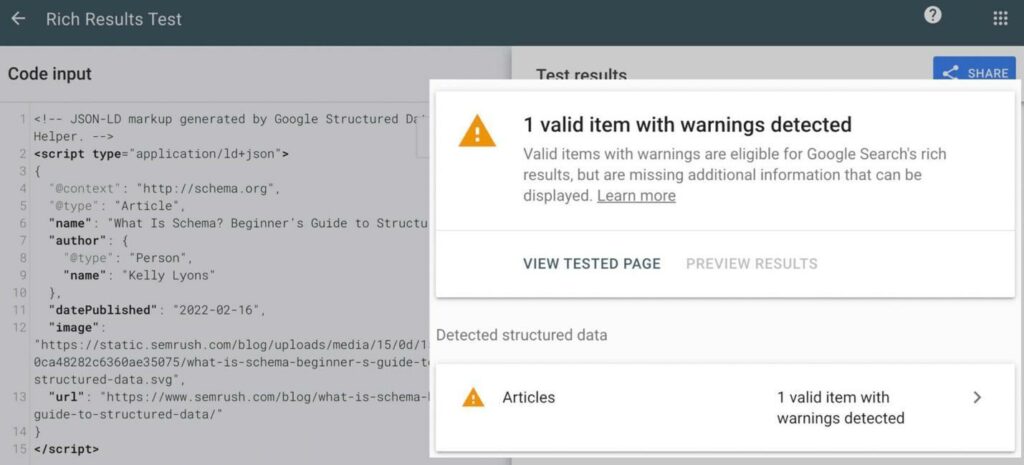
You can then fix the flagged areas directly on the tool. That way, you can be sure that your schema markup will help boost your search rankings and keep you protected at the same time.
Balancing Mobile Security with Google Mobile-First Indexing
Mobile security in the post-pandemic workplace should no longer be limited to cell phones and tablets.
With businesses adopting remote work and Bring-Your-Devices (BYOD) policies to help boost job satisfaction and reduce overhead costs, ensuring that your cybersecurity policies align with these changes is critical.
Here are some tips to help you update your mobile cybersecurity policies to keep your business protected:
Employ Multifactor Authentication
At first, multifactor authentication can be a nuisance because it’ll require you and everyone else in your business to undergo several verification steps before accessing the tools you use at work.
However, these additional steps mean that different layers of security are put in place on your devices, making them more secure for you and your employees to use at home, in a co-working space, or at your favorite coffee shop.
Secure Your Online Forms
Mobile device users make up 56.2% of the traffic visiting websites, including yours!
Unfortunately, mobile devices also account for 73% of significant cybersecurity breaches experienced by businesses.
That said, it’s vital to ensure your website is user-friendly for mobile device users and secure to prevent malware from getting into your website through your contact forms.
One way to secure your online forms is by adding data encryption and security tokens like reCaptcha.
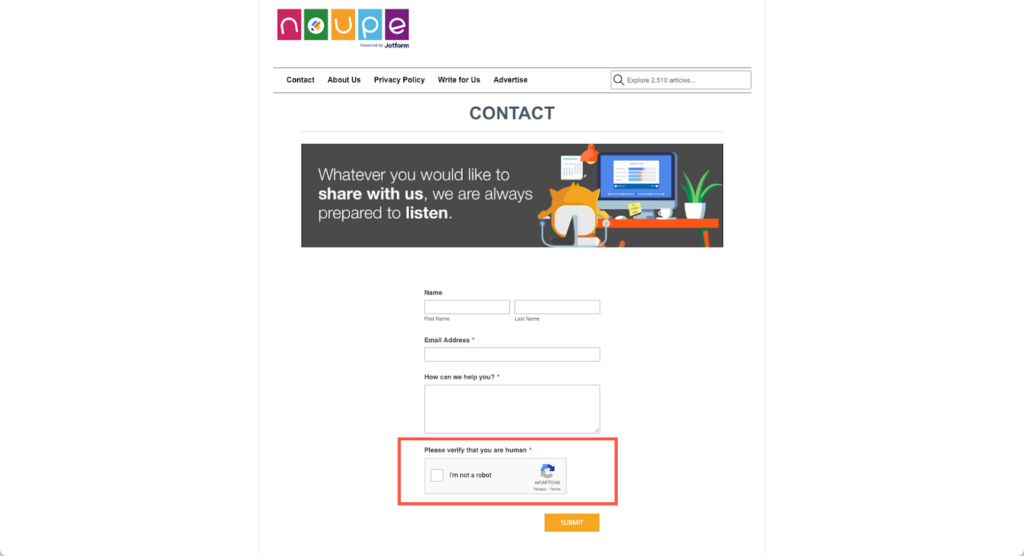
This helps prevent your business from getting flooded with spammy responses, including malware cybercriminals can use to steal sensitive information and hostage your website for ransom.
Be Diligent When Granting Internet Access
This is particularly important if you’re implementing a hybrid work model and BYOD policy in your business.
Since cybercriminals know that personal devices are less secure than those furnished by companies, they would use these as an entry point to hack your system.
Restricting the number of devices that can access your internet can help significantly reduce the chances of this happening.
Ensuring Cybersecurity During SEO-Focused Site Migration
Migrating your website to a new web hosting provider is risky and should never be taken lightly.
For starters, you must take down your site to begin the process.
When that happens, your target audience and search bots won’t be able to access you’re website, causing your search and domain rankings to drop.
Part of the site migration process involves temporarily disconnecting any security measures you have in place, leaving your website and business vulnerable to data breaches and other cyber attacks.
On top of that, you run the risk of potentially losing content and valuable data about your customers.
Before starting the site migration process, back up your entire website onto an external drive. That way, you eliminate any chance that cybercriminals can get access to it.
Also, conduct a comprehensive website and SEO audit once the site migration is finished and before you bring your website back up. This allows you to thoroughly check your website to ensure there are no errors and vulnerabilities that’ll serve as a backdoor for cybercriminals to enter and wreak havoc.
Finally, submit your sitemap and robots.txt to Google through your website’s Search Console account. This will prompt Google bots to start crawling and indexing your newly migrating site and display it on its SERPs again.
The Interplay of AI in Future Cybersecurity and SEO Strategies
Artificial intelligence (AI) technology advancements are both a blessing and a curse.
On the one hand, AI has made it easier for businesses to adapt their SEO strategies to ever-changing industry trends and customer behaviors. It’s also helped streamline workflow processes, increasing employee productivity and job satisfaction.
These same advancements, however, equipped cybercriminals to become more sophisticated in their infiltration techniques.
AI writing tools like ChatGPT are a perfect example of this.
ChatGPT can help businesses and cybercriminals write personalized and compelling email copy to convince readers to act.
Not surprisingly, the number of people and businesses victimized by email phishing spiked by a whopping 1,265% since ChatGPT launched.
That’s why cybersecurity professionals are deploying and enhancing AI-powered cybersecurity solutions that recognize patterns in malware code and scripts used by cyber criminals, allowing them to block these before they can do any damage.
AI-powered cybersecurity solutions can also help identify and address negative SEO tactics like link farming, artificial traffic, and bots filling out forms on your website.
Conclusion
As long as the internet exists, cybercriminals will always be out there, ready to attack your website when the opportunity presents itself.
The tips and strategies shared in this article won’t eliminate the threat of a cyber-attack. But they can significantly reduce the chance of your business becoming a victim if you diligently put them into practice.
The war against cybercrime can’t be won’t a few people within your business. Everyone has a role to play. Creating a cybersecurity policy and having open communication with your employees ensures that everyone will do their part in protecting your website and themselves from cyber criminals.
Featured image by Dan Nelson on Unsplash